How to Protect Your VPS Hosting from DDoS Attacks?
Ddos-attack seems to be one of the most widely known hacking tricks. Not all of internet cheaters want to steal your money or to seize personal data of yours, some of them are just interested in disrupting your business and hindering a normal function of your site. This kind of attack isn't random, that is planned and coordinated set of actions, which is aimed to make you web page unavailable by overwhelming it with traffic from multiple sources.
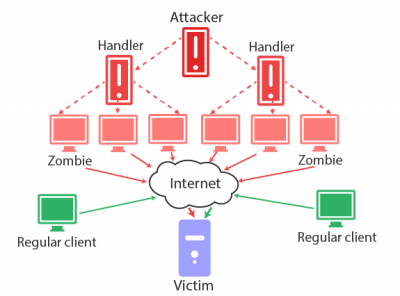
Researchers claim one third of all downtime incidents are attributed to DDoS attacks. So it’s a justifiable threat for your site credibility that can cost you a reputation and provoke visitors to float away. When you have a site on a VPS hosting, you also can’t be sure it is protected enough. To know how to protect vps hosting from ddoss attacks, you should know some basic rules and our team will help you in that matter. We have prepared some recommendations about vps ddos protection, so hope they will be useful.
Upmost things you should check and configure
If site is located on VPS hosting, it is possible to determine a level of an attack on your own. You can temporarily disconnect your web server and analyze its logs. In case you feel protection against DDoS attacks is not your profile or you need a real practical advice, it is better to ask the virtual server administration specialists.
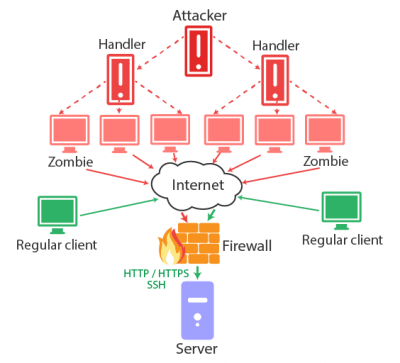
Firewall
The first step to achieve DDos protected VPS is to configure your firewall correctly and to use it actively. However, before installing or configuring the firewall, stop the services you don’t need. It is a bad idea to run another services on web server containing sites, so try to create for them a separate VPS. Firewall enables to close all the ports, keeping open only http, https and ssh. The thing is that browsers of visitors connect exceptionally to http or https, so connections to other ports don’t belong to real people and should be rejected. It is also recommended to move your ssh server (for an administrator) to another non-standard port.
Vps ddos protection also includes checking headers of incoming packets for matching stacks of TCP protocol. Web bots often use incorrect packets to exploit vulnerabilities of server software for making it either crash or hang up.
Protection from HTTP, ICMP, ICMP, UDO and SYN-flood
To provide a protection against DDoS attacks it's essential to determine the type of an attack whether it may be HTTP, ICMP, ICMP, UDO or SYN-flood and then decide what countermeasures to implement.
Http flood is one of the simplest Ddos attacks caused by attacking side forcing the server to allocate the maximum resources possible in response to each single http request (GET or POST). To mitigate http flood attack you should have a properly configured and optimized web-server. To choose between Apache and Nginx experts recommend to prefer the last one as it takes less resources and is more stable. For avoiding any interference to machine’s uptime you can also analyze site’s access log and then write a pattern using that results. It will allow you to define and ban all bots’ requests.
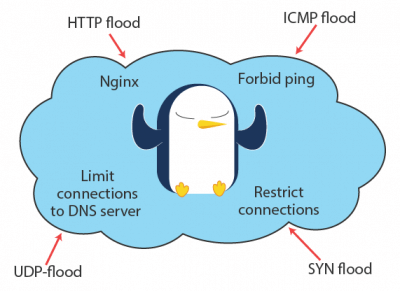
ICMP flood means sending of an abnormally large number of ICMP packets (Internet Control Message Protocol) of any type, especially «ping» packets, so another good tip to make your web host more reliable is to forbid ping for hiding your machine from Internet bots that are scanning your network.
The attack which involves repeatedly sending of SYN (synchronization) packets to every server’s port using fake IP addresses is called SYN flood. To defend web hosting from this trouble one should figure out the connection in SYN_RECV state and restrict the new connections from a certain source for a certain time period.
To make a protected cloud server you should also consider an UDP-flood. In that case attacker sends a huge amount of UDP (User Datagram Protocol) packets to single or random ports of remote server mainly for saturating Internet pipe. You can protect you server from this kind of attack by limiting connections to DNS server.
Fail2ban
If you want to boast of your protected linux vps from ddos attacks, we also advise you to install fail2ban. Usually it doesn’t include in a base set of utilities, so you have to find it independently. Fail2ban from a box has already some filters for the web servers, but it’s better to set your own. To secure a DDos protected VPS you should also configure your virtual hosts in a way that logs for all sites must be common. It enables you to protect your sites by using only two filters, so you’ll sleep well instead of bothering how to protect vps hosting from ddoss attacks. Using fail2ban you can also make your ssh server more reliable, so be sure nobody will make an attempt to your administration right.
Prevention is better than cure
However that may be, to prevent Ddos-attacks is much more effective than fighting with it. In order to keep you site high-load and Ddoss-attacks-free you should always upgrade your server’s software, install additional patches and modules for your vps ddos protection and correctly configure all the servers on your VPS. Taking into account all the information above, the best way to be protected is to choose the reliable VPS hosting provider such as Tucha cloud and to redirect all these tasks to the specialists. We permanently monitor your system to prevent any difficulties. With Tucha cloud team any attack on you VPS will be failed, don’t have any doubt!


No Comment